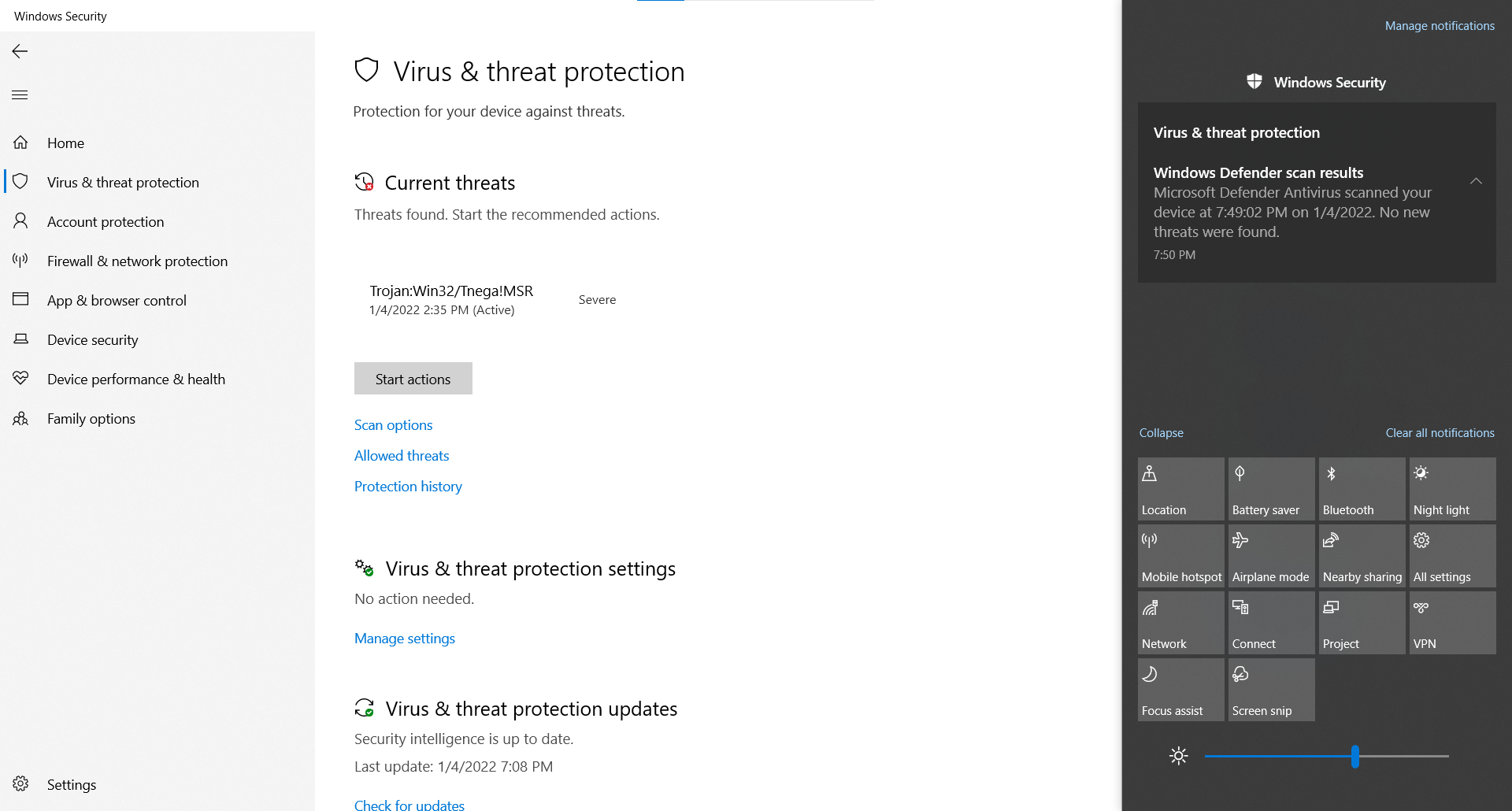
To make sure that you detect all possible Trojan infections, in addition to at least two virus scanners on a Windows computer, it's also recommended to run a full scan with Windows Defender Offline. This can help to detect and remove particularly stubborn Trojans using the latest threat definitions.Can Windows Defender remove Trojans Windows Defender cannot remove all Trojans from your device. There may be additional steps you have to take to remove them. Make sure Windows Defender performs a virus scan.Microsoft Defender's real-time anti-malware protection runs whenever your device is on, keeping an eye out for malicious activity. Microsoft Defender will also run quick scans of your device on a daily basis, in case anything manages to elude the real-time protection.
Can Windows Defender detect hackers : If Defender detects unusual activity, it alerts ITS staff that a hacker may be present in the system. "Every Windows and Mac OS computer has antivirus built in," Tener said, "but the new way hackers are compromising computers isn't just using a known bad app.
Can Trojan go undetected
Trojan viruses are a type of malware that invade your computer disguised as real, operational programs. Once a trojan is inside your system, it can perform destructive actions before you even know it's there.
Can Trojan hide from antivirus : Rootkit technologies – that are generally employed by Trojans – can intercept and substitute system functions to make the infected file invisible to the operating system and antivirus programs. Sometimes even the registry branches – where the Trojan is registered – and other system files are hidden.
To find it, the user must initiate a full computer scan with an anti-virus scanner. This should be able to identify all threats and inform the user of the name of the malware. In addition, the scanner usually recommends the necessary measures to completely remove the Trojan and the installed malware from the system.
Yes, malware can hide itself and antivirus and other protection programs may not catch it. Check out this undetected malware map.
Can Windows Defender detect fileless malware
Through AntiMalware Scan Interface (AMSI), behavior monitoring, memory scanning, and boot sector protection, Microsoft Defender for Endpoint can inspect fileless threats even with heavy obfuscation. Machine learning technologies in the cloud allow us to scale these protections against new and emerging threats.Microsoft Defender Antivirus detects and protects against the following kinds of threats: Viruses, malware, and web-based threats on devices. Phishing attempts.Because Trojan malware is delivered inside a legitimate app or file, it's very difficult to detect. Trojans are used to spy on victims, steal data, infect other programs, and inflict other harm. Trojans are typically sent by scammers or hackers who use social engineering tactics, like the ones used in phishing attacks.
To find it, the user must initiate a full computer scan with an anti-virus scanner. This should be able to identify all threats and inform the user of the name of the malware. In addition, the scanner usually recommends the necessary measures to completely remove the Trojan and the installed malware from the system.
Is it OK to have Trojan virus : Are Trojan viruses bad Trojan viruses are bad because they trick users into downloading malware that harms devices in various ways. As an example, remote access Trojans (RATs) give hackers remote access to infected computers, which can result in spying, data theft, and identity theft.
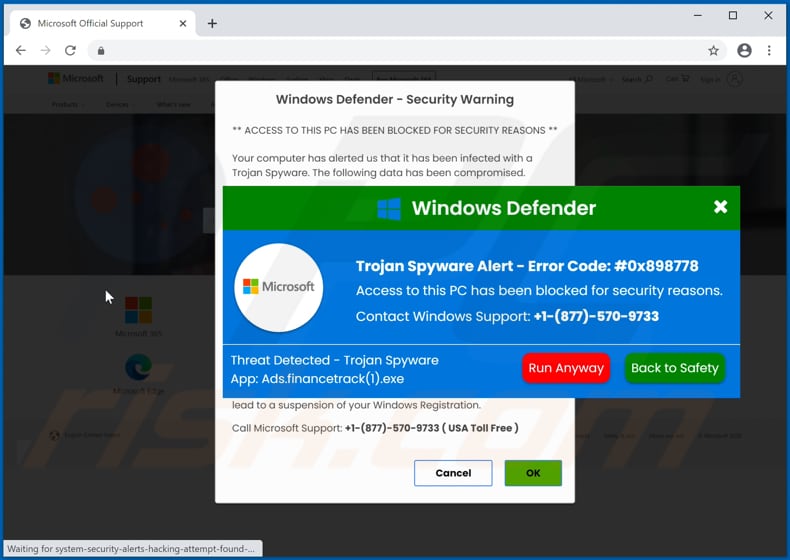
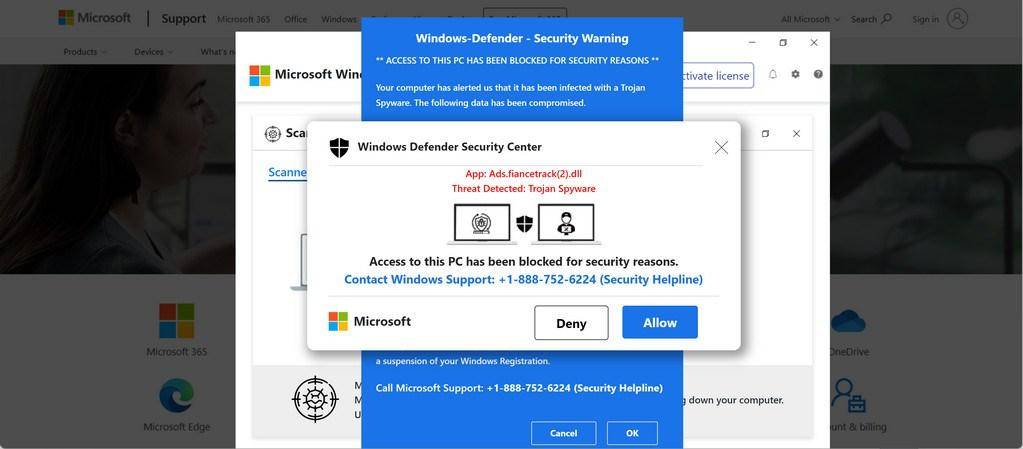
Is Trojan easy to detect : That's why Trojans can be so hard to detect — they look like legitimate software. The best way to protect yourself against Trojans is with reliable security software that can detect, block, and remove all kinds of malware and viruses automatically. That way, there's no chance for the Trojan to trick you.
Can viruses bypass Windows Defender
Windows Defender is very good for the price it asks. It's free so you can't complain much. Sadly, there are many viruses Windows Defender can't detect and remove.
Malwarebytes Endpoint Detection and Response (EDR) offers an effective solution to detect and mitigate fileless malware threats by monitoring potentially malicious behavior on endpoints.Because keyloggers are a form of spyware, you can use a reputable anti-malware program that scans your device and automatically removes spyware from your operating system. Microsoft Defender, built into Windows 11 and Office 365, can actively monitor your system for spyware such as mobile keystroke loggers.
Does Windows Defender scan everything : Windows Defender will now initiate a thorough scan of your entire system, including all files and folders.