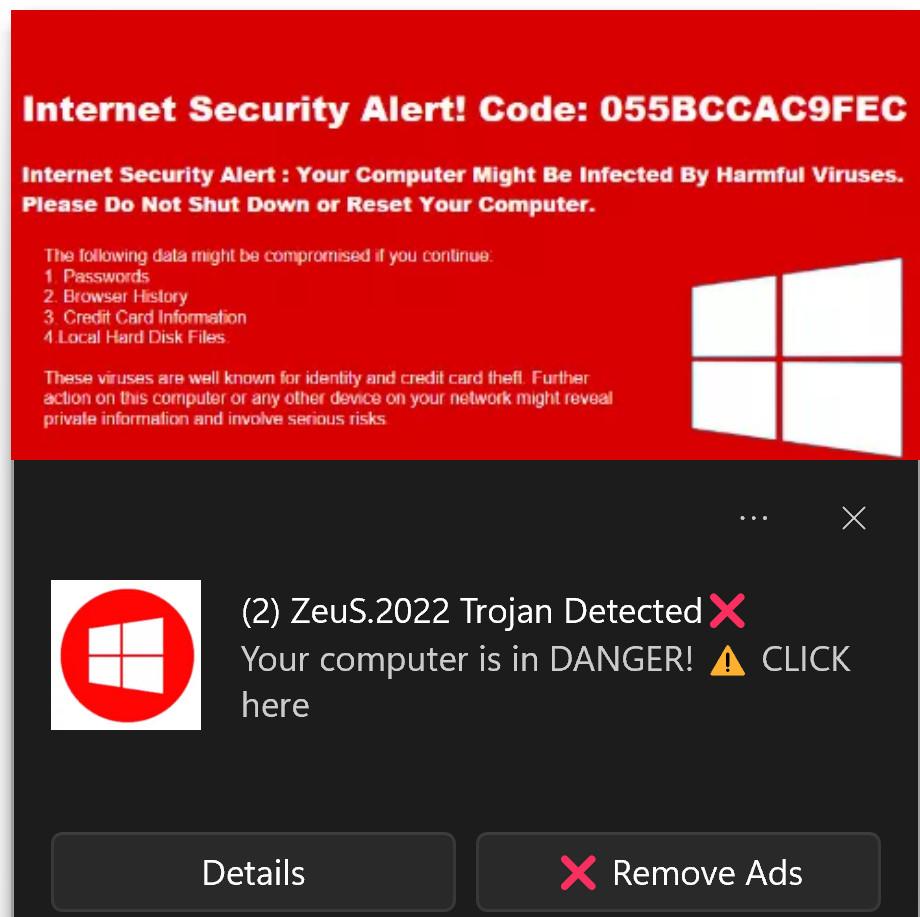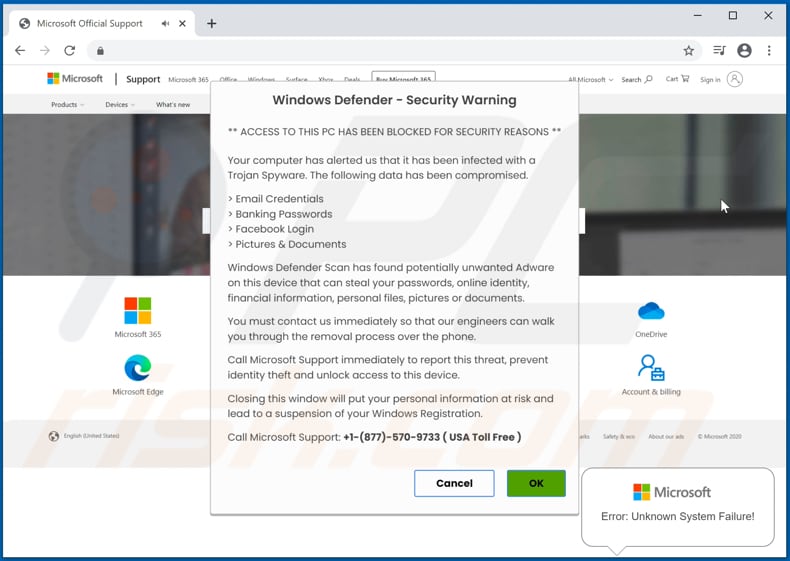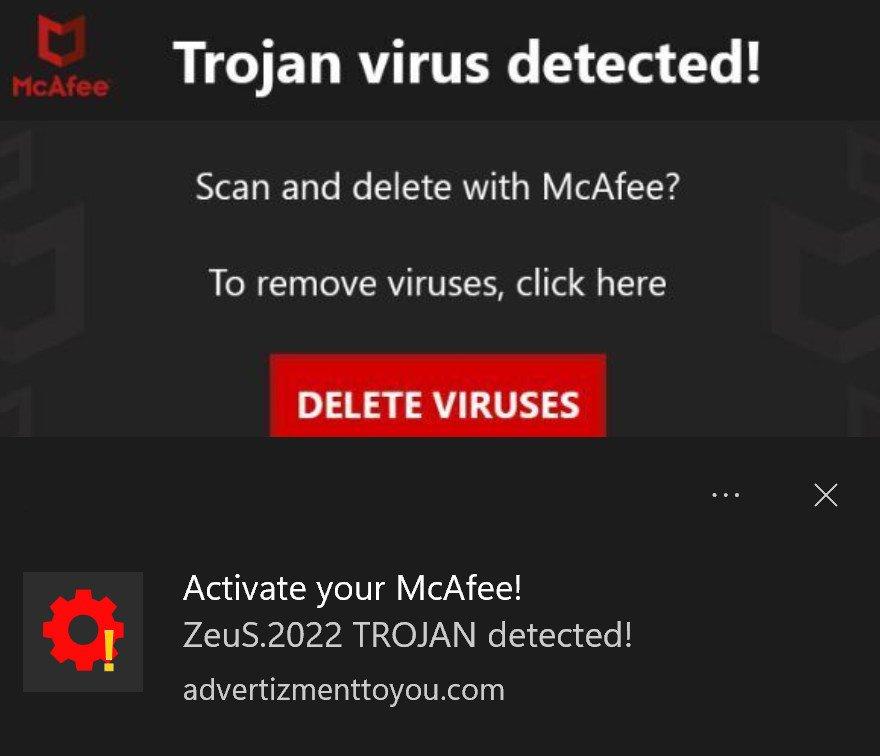
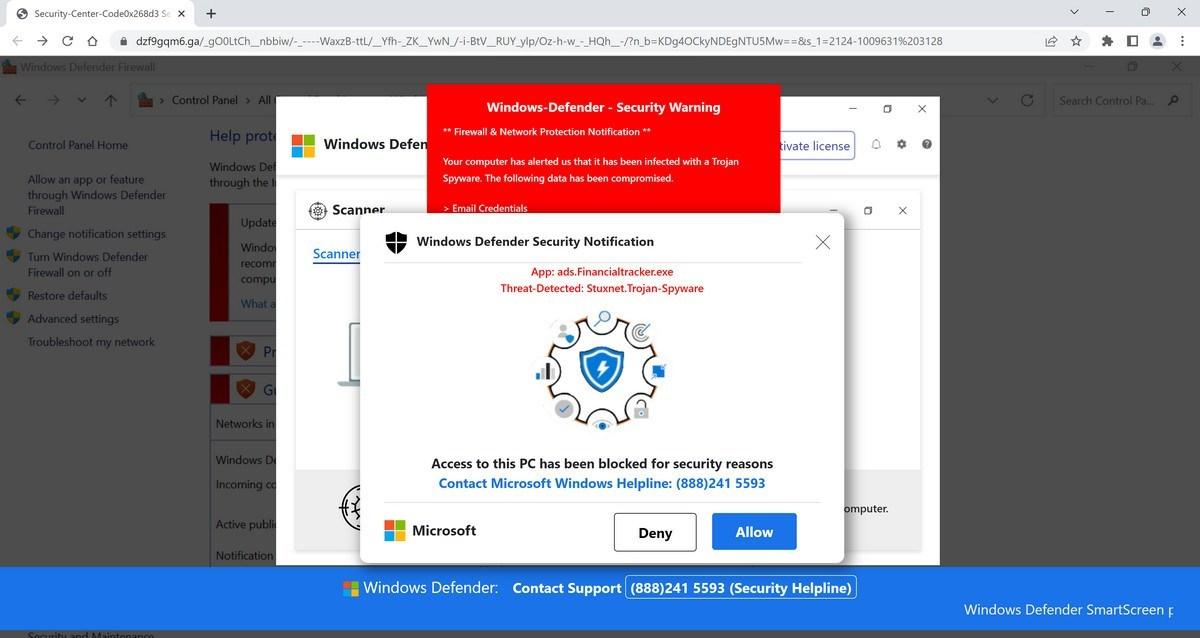
Common types of phone malware and viruses
Trojans: Trojans refer to malware bundled within legitimate-looking applications or downloads. You may think you're only downloading a new mobile game or flashlight app, but in this case, there is also malicious code embedded within the program.However, you can detect a Trojan by observing your devices, programs, and apps.
- Check your programs and apps. Check your computer's software programs and mobile device's apps regularly.
- Check your startup programs. Trojans can also hide in your computer's startup process.
- Check your device's performance.
Installing and using a trusted antivirus solution is also one of the top ways to get rid of trojans. An effective antivirus program searches for valid trust and app behavior, as well as trojan signatures in files in order to detect, isolate and then promptly remove them.
Can a Trojan virus spy on you : These programs can cost you money – by sending text messages from your mobile device to premium rate phone numbers. Trojan-Spy programs can spy on how you're using your computer – for example, by tracking the data you enter via your keyboard, taking screen shots, or getting a list of running applications.
Should I worry about Trojan
The harm that Trojans can cause extends beyond just individual computers. Cybercriminals can use Trojans to create a botnet, which is a network of infected computers that a malicious actor can remotely control to spread malware or stage other online attacks.
Can Trojan destroy my PC : Botnet recruitment: Some Trojan horses are designed to convert infected computers and pull them into a botnet that cybercriminals can control remotely. Data destruction: Certain Trojans may be programmed to delete files, corrupt data, or even reformat entire hard drives.
A computer infected by Trojan malware can also spread it to other computers. A cyber criminal turns the device into a zombie computer, which means they have remote control of it without the user knowing. Hackers can then use the zombie computer to continue sharing malware across a network of devices, known as a botnet.
Trojans are disguised as legitimate files, but they have one goal: to trick you into clicking, opening or installing them. If they're successful, this triggers the Trojan to download malware onto your device or begin spying on you.
Do Trojan viruses go away
To remove Trojan Viruses and other malware from your PC, follow these steps: STEP 1: Use Rkill to terminate malicious processes. STEP 2: Uninstall malicious programs from Windows.A drive-by download is a cyber attack that refers to how viruses and malware get installed on user's devices – without the user knowing it's being downloaded. Drive-by downloads don't require the user to click on anything on a webpage.Trojan viruses can not only steal your most personal information, they also put you at risk for identity theft and other serious cybercrimes. In this post, we'll examine what Trojan viruses are, and where they come from.
Trojan viruses can not only steal your most personal information, they also put you at risk for identity theft and other serious cybercrimes.
Can Trojan destroy your PC : Trojan attacks have been responsible for causing major damage by infecting computers and stealing user data. Well-known examples of Trojans include: Rakhni Trojan: The Rakhni Trojan delivers ransomware or a cryptojacker tool—which enables an attacker to use a device to mine cryptocurrency—to infect devices.
Is .exe always a virus : An .exe file can be a virus, but that is certainly not true for all of them. In fact, the majority are safe to use or even necessary for your Windows system to run. It all depends on what is in an .exe file. Basically .exe files are programs that have been translated into machine code (compiled).
Is trojan spyware real
Yes, unfortunately, Trojan spyware viruses can steal your personal information. They can also disrupt your machine's performance, steal files that are saved on your device, or even give hackers the means to control your device remotely. This can lead to cyber criminals turning on your camera and microphone.
The Chrome.exe virus, or Poweliks trojan, is a Trojan horse malware that disguises itself as a legitimate computer program to evade detection. The ".exe" means it's an executable file.If you're not sure about a file, don't open it. Exe files from unknown sources can contain viruses or malware that can harm your computer. When it comes to downloaded files, it's always best to err on the side of caution. Unless you're absolutely positive that a file is safe, don't open it.
How do I delete a Trojan : How do you remove Trojans
- Step 1: Disconnect internet. Before you start removing the Trojan, make sure that you disconnect from the internet.
- Step 2: Launch antivirus program.
- Step 3: Remove Trojan in Safe Mode.
- Step 4: Perform system recovery.
- Final option: Reinstall Windows 11.